
How to Implement IoT Within Modern Software Solutions
Software technology is boosted by the backbone ‘of the Internet of Things (IoT).’ Industrial automation and smart living spaces are enabling IoT implementations and driving smarter, more efficient industry operations. The use of IoT capabilities already completely deployed into the software realm does not stop at simply pairing things. It requires knowledgeable integration, deep security, and expandability, which are made simple.
The key task of this article is to go deep into the best practices of IoT in software development by beginning with its transformation capacities. In this post, we’ll explore the fundamentals of high-level design, proceeding through connectivity and data management and securing and testing data-driven applications. Whether creating an easy smart device or a sophisticated IoT environment, these tips will help you on your road.
Understanding the Role of IoT in Software Development Today
The Internet of Things (IoT) changes the meaning of software – it secures a transition, closing the real-life gaps. The key to IoT is that the machines, sensors, and devices can speak, share, and answer information in real time for software developers. It means writing software that can communicate and manage hardware and frequently getting its hands on masses of information to provide smarter, more tailored experiences to users.
Enhanced User Experiences
Smart wearables and smart home technology that learns and adapts to individual preferences are possible with IoT.
Automation
IoT software works with industry manufacturing and logistics, using IoT to streamline operations, thus increasing efficiencies and minimizing the man-hours involved.
Data-Driven Decision Making
So, IoT software collects information from smart, networked devices and helps in smarter decision-making, such as predictive maintenance or analyzing customer behavior. However, the most important thing is recognizing the value of IoT transformation, which takes only one step. For developers, it needs to be integrated, secured, scaled, and there to unlock its full potential. Knowing these dynamics, companies can create software programs for IoT devices that not only make them work but also innovate in a world that’s becoming more connected.
Key Design Principles for IoT Software
It is a complex and specialized task to develop software for IoT: the function must overlap with dependability and expansibility. HVX software is less orthodox than conventional programs in that it not only transmits with various gadgets but also works with constant strings of information with no application of efficiency. It must comply with any realm of important axioms to make it a reasonable and solid IoT solution.
This software will remove integration between different categories of hardware. Along with scalability, it is enough because IoT systems are growing with more and more devices and users.
- Edge processing can leverage edge processing for localized information processing to reduce bandwidth usage and latency. However, cloud integration also calls for storing and analyzing the information centrally with both worlds’ best capabilities.
- IoT devices are limited by finite power sources and, hence, must process and transmit requirements as efficiently as possible, minimizing them as much as possible in both cases.
- IoT software must be simple for the users. However, it doesn’t matter what kind of platform your delivery will be – web platform or smartphone app – usability must be everywhere, and always it must be delivered in the form of an unproblematic use for end users.
- Fail-safe mechanisms and redundancy are implemented to prevent disruptions from taking out devices or to recover quickly.
If developers combine the above design fundamentals for IoT-powered software, the software will be efficient, friendly, and flexible enough to react to changes in requirements and thus ensure long-term success.
At Cleveroad, we help businesses implement IoT within modern software solutions by designing scalable architectures, ensuring secure device connectivity, and building reliable data pipelines from edge to cloud. Our team works with connected platforms across industries — from smart home and wearable ecosystems to industrial automation — focusing on solutions that are efficient, user-friendly, and ready to grow with expanding device networks. With hands-on expertise in IoT integration and full-cycle software development, Cleveroad can support you in turning connected device concepts into stable, production-ready systems.
How to Ensure Security and Privacy in IoT Integrations
Nowadays, security and privacy are, of course, high concerns when it comes to extending software offerings with IoT capabilities. A single weakness in a single device within such a high volume of IoT devices sending sensitive information will result in a big leak. The role of developers in securing IoT environments is as active as possible, somewhere between desired connectivity and protecting the users’ data.
End-to-End Encryption
For data to be encrypted, it must be encrypted so that no one is allowed to read, let alone access, the data while it is in transit and, most importantly, at rest. The information will also not be readable to hackers even if it’s intercepted utilizing powerful encryption protocols.
Secure Authentication Methods
The implementation of multi-factor authentication (MFA) and device identifier mitigates the unauthorized access to IoT networks by authenticating a device and the legitimacy of a user.
Regular Software Updates and Patches
Old firmware and software vulnerabilities turn IoT devices into a target. Systems that are updated regularly, and have automated patch management, are more secure against new threats as well as yet-to-be-known threats.
Data Minimization
Only collecting critical information reduces the opportunity for exposure. The only way to group and anonymize sensitive information is to maximize the user’s anonymity.
Comprehensive Security Testing
The security measures must be tested in detail by vulnerability scans, penetration tests, and code reviews. When a weakness in the software stack is discovered early, some of the pennies that would be spent to remediate the breach later are saved.
Developers can set up trust and security by prioritizing security and privacy at each phase of the IoT integration. By doing security at every level, developers will be committed to not just mitigating potential vulnerabilities but also laying a good foundation for the successful realization of IoT.
Best Practices for Smooth Handling and Integration of Data
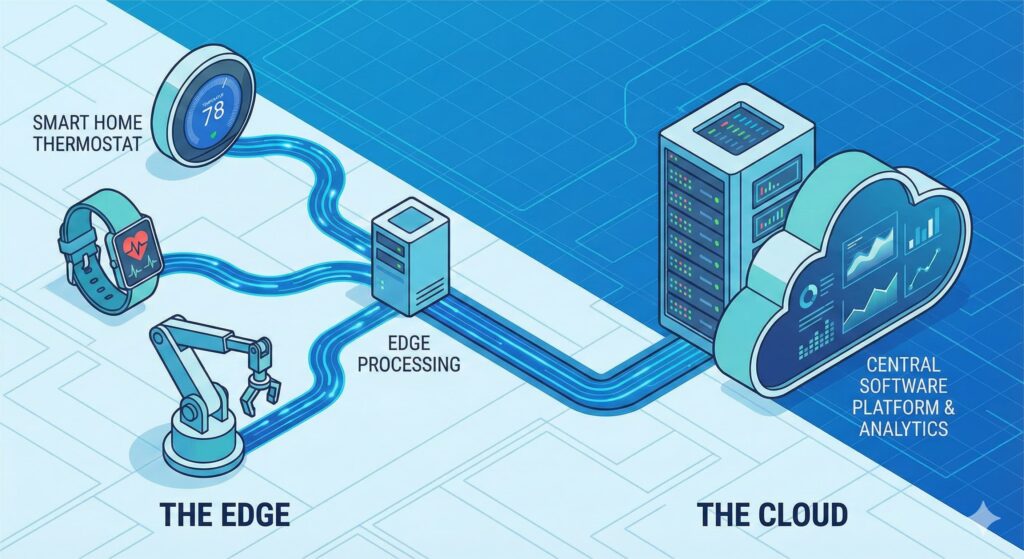
Any IoT-powered solution starts with effective data management and connectivity. However, IoT systems generate huge amounts of data that need processing, storage, and transfer efficiently. You have to strategize how you want to develop data flow so that the ecosystem connected is stable and the performance is smooth.
Include a Tiered Data Processing
Edge computing is used for real-time data analysis and cloud-based development for large-scale data processing and storage. This allows for the scalability of complex data analytics while also reducing latency.
Implement Robust Data Filtering
All IoT data is not of equal value. Filtering and prioritizing data at the device level means you are not putting extra load on the network and saving on storage costs without losing out on valuable insights.
Choose Reliable Communication Protocols
If you have low bandwidth requirements, favor lightweight protocols such as MQTT or CoAP and check that your devices are compatible with the underlying communication protocol. When reliability is critical, you want low-latency protocols.
Optimize Network Redundancy
Growing disruption in connectivity can affect the performance of IoT. When the networks are redundant or fall over mechanisms used, the communication continues even when the network goes down.
Enable Scalable Storage Solutions
Manage increasing volumes of data using cloud-based auto-scaling storage. This goes well with efficient database designs for IoT data, like time series databases.
Prioritize Interoperability
Create systems attractive to device manufacturers and software platforms that run smoothly while enabling easy communication between them.
Following these best practices, developers can build IoT solutions capable of handling large data flows while also keeping the device communication consistent. This is not only a reliable, future-proofed system for any complex IoT ecosystem but also a system that meets the now and the future.
Testing and Scaling IoT-Integrated Software Solutions
The need to test and scale up with increasing complexity is also one that is growing with IoT solutions. This includes testing that the system is reliable to work across multiple devices, environments, and use cases, and scaling, where we make sure your IoT software can scale to handle more devices, as well as more data, without a decrease of performance. However, both of them are essential for the long term success any of the IoT solution.
Comprehensive Device Testing
IoT systems have to have the ability to interact with a wide range of devices, each with different capabilities. Your software must be accessible for different device types, manufacturers, and operating systems. Testing and simulating real-world scenarios is meant to uncover hidden issues with inter-device connectivity.
Network and Latency Testing
In the case of IoT, it’s very important because IoT relies on continuous communication, so your software should work well on various network conditions. Run your system under various situations, including high latency, connections that are not always there, and network congestion, so that you can see how real-time data transmission through that system might be serviced by it.
Stress Testing for Scalability
With the growing demand for IoT ecosystems, the number of devices, as well as the size of the data, are increasing exponentially. This stress testing allows us to assess how your software will function under such heavy loads and ease the surge of devices and data without crashing or reducing performance. Make sure your system is horizontally scalable to deploy more servers and maintain a load balance among them in case of an increase in load by using a cloud environment or multiple servers.
Automated Testing Software
Especially for the huge IoT deployments, automated testing tools can speed up the testing process and provide better results. Automated scripts can be used to run simulated device interactions, check connectivity scenarios, and test for vulnerabilities. Regression testing is especially useful through automated testing, as well as by automated testing generally when the software or devices are updated.